How often have you gotten a social media connection request from a person you didn’t know well, or perhaps even at all? Did you reject it immediately, accept, or do a little research first? Many people skim the profiles of potential connections to determine the validity of an unknown request—that is, the perceived validity. What if those seemingly random requesters were actually members of an Iranian-based threat group intending to silently spy and eventually steal your data?
No, this isn’t the intro to the next spy blockbuster hit. It’s the true story of a targeted, multi-layered attack carried out through the popular social media platform LinkedIn—an attack discovered by Dell SecureWorks Counter Threat Unit (CTU) researchers who had been tracking Iran-based Threat Group-2889 (TG-2889).
Haven’t heard about it yet? Dell’s report, released earlier this month, comes to us smack in the middle of National Cyber Security Awareness Month. Let’s talk about exactly what happened, how Dell uncovered the breach, and what we can learn from it all.
The Scenario
I’ll break it down for you: Say you get a LinkedIn request from a recruiter from General Motors—or, who you believe is a recruiter from General Motors. You think, “why not?” and accept. After all, that person has a good looking profile with plenty of other connections who also seem reputable. The only difference between that Iranian hacker “recruiter” and a real General Motors recruiter is that only one of them is going to send you malicious malware in a resume application lookalike email, compromising your computer and all its data. (Hint: Stay away from door number one.)
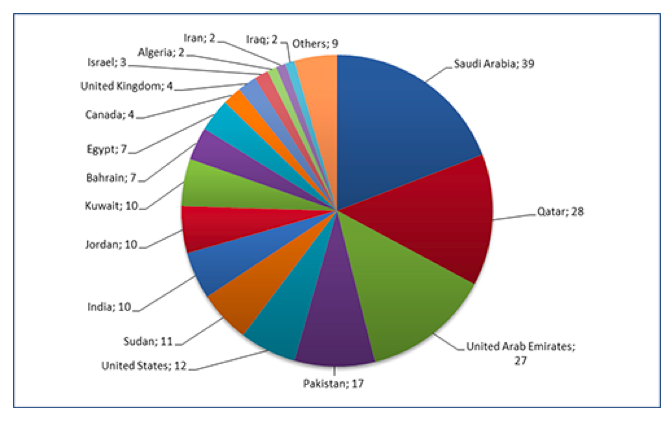
We’ll explore the whole report in a minute, but here is an overview: Cyber spies from TG-2889 were using LinkedIn profiles to pose as recruiters from well-known worldwide companies like Doosan, Airbus, General Motors, and more. The 25 profiles discovered had more than 200 legitimate LinkedIn connections from unknowing members. Most targets worked in government, telecom, or defense sectors, and hailed from Pakistan, Quatar, Saudi Arabia, and the United Arab Emirates. Twelve were from the United States. The hackers spied on these targets using social engineering—in other words, they researched them on social media to up the ante on their phishing attack.
Dell Security’s Discovery
Dell’s CTU is a team of researchers that “…actively monitors the cyber threat landscape and performs in-depth analysis of emerging threats and zero-day vulnerabilities.” The group specializes in reverse engineering, cybercrime investigation and malware analysis (among others).
In discovering the Iranian-led LinkedIn cyber spying operation, CTU found that hackers had set up two types of fictitious profiles: Leader personas included full education and professional history, while supporter personas were much lighter on information and connections (each having only five). The role of the supporter personas was to add credibility to the leader personas through skill endorsements. Once this perceived “connection” was built, CTU found that the cyber attackers used phishing to distribute malware to targets in professional-looking messages.
Report Highlights
The full report from CTU, including a table at the bottom with identifying information for the 25 falsified profiles—is available here. In the meantime, let’s go over some highlights.
Who exactly was targeted? CTU reported that about a quarter of the targets of this cyber attack work in the telecommunications vertical, especially Middle Eastern and North African mobile telephony suppliers. Another significant finding was that several of the targets worked for Middle Eastern governments and South Asian-based defense organizations. Below is a graph showing the legitimate endorsers—those who were the victims of the cyber spying—and their locations.
Have we seen this before? Not too long ago, cyber security company Cylance released the December 2014 Operation CLEAVER report describing how threat actors (read: phonies) can use malware that looks similar to a job application or resume submittal service. The following domains—also linked to the profiles in this recent Iranian LinkedIn scandal—were cited in the report: Teledyne-Jobs.com, Doosan-Job.com and NorthropGrumman.net. It was thought at the time of Cylance’s report, just as it is expected now, that the threat group at work here is Iranian.
Cyber Security Takeaways
There was something different about this hack, something a bit more involved than simply spamming your email with links obviously laden with malware. This layered cyber attack utilized social media—a social media platform geared toward professionals who should, by all rights, know better. Right? Maybe so, but we’re all human and it can be hard to differentiate the well-intentioned from the sinister, especially from behind a keyboard. The good news here, besides the fact that the CTU researchers caught the breach, is that we can still learn a few things. Here are some cybersecurity points Dell wants you to take away from its report:
- It’s not over yet. These identified fake TG-2889 profiles are maintained and updated regularly. Profile adjustments indicate the hackers may be moving in a more targeted direction, perhaps targeting the aerospace vertical. CTU found 25 hacker accounts, but there could be more that have yet to be discovered.
- Be smart on social. You should absolutely avoid contact with the falsified personas should it be initiated. Only connect to people you personally know, and use “sensible caution” when it comes to friends of friends. Using LinkedIn for employment? It may not be the best time to go through social media channels for that purpose, unless you can independently verify the opportunity. Otherwise, if you see something you want to pursue, contact the company directly.
- Protect your business. Take a look at how your brand is represented on LinkedIn (and other sites). Are the people who claim to work for you really there? If you discover anything that doesn’t belong, contact LinkedIn to have the falsified content removed. (It’s against their terms and conditions).
This cyber attack should have all of us taking a hard look at our behavior on social media sites like LinkedIn (and others). Don’t get me wrong—it’s undeniable that social media sites are chock full of personal and professional networking opportunities, and a lot of good comes from these connections. Perhaps, though, every once in a while, it doesn’t hurt to be reminded that our guard should still be in place, especially in (online) social situations. How do you feel about this LinkedIn hack? Will you be doing anything differently with your connections in the future? Are there other topics you’d like to talk about during Cyber Security Awareness Month? I’d love to hear your thoughts.
Additional Resources on this Topic:
The S.A.F.E Method to Hack-Proof Your Social Media Accounts
Social Media: Why We Share Things Online
Criminals Are After Your LinkedIn Account – Here is How to Protect it
This post was written as part of the Dell Insight Partners program, which provides news and analysis about the evolving world of tech. For more on these topics, visit Dell’s thought leadership site Power More. Dell sponsored this article, but the opinions are my own and don’t necessarily represent Dell’s positions or strategies.
photo credit: Hacker, Diebe, Sensationen 330/365 via photopin (license)
Shelly Kramer is a Principal Analyst and Founding Partner at Futurum Research. A serial entrepreneur with a technology centric focus, she has worked alongside some of the world’s largest brands to embrace disruption and spur innovation, understand and address the realities of the connected customer, and help navigate the process of digital transformation. She brings 20 years' experience as a brand strategist to her work at Futurum, and has deep experience helping global companies with marketing challenges, GTM strategies, messaging development, and driving strategy and digital transformation for B2B brands across multiple verticals. Shelly's coverage areas include Collaboration/CX/SaaS, platforms, ESG, and Cybersecurity, as well as topics and trends related to the Future of Work, the transformation of the workplace and how people and technology are driving that transformation. A transplanted New Yorker, she has learned to love life in the Midwest, and has firsthand experience that some of the most innovative minds and most successful companies in the world also happen to live in “flyover country.”